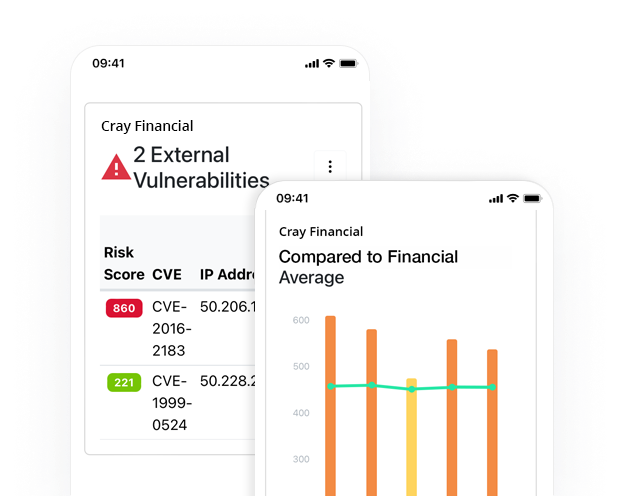
TARA CTA meets the cyber protection needs of small and medium businesses for vulnerability management, but it’s also packed with enterprise features. Refer to the table below to see how its features stack up against the competition.
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Category | TARA CTA | Bitsight | Security Scorecard - Free | Security Scorecard - Business | Security Scorecard - Enterprise | Security Scorecard - Max | IBM - Security Randori Recon Essentials | IBM - Security Randori Recon Standard | IBM - Security Randori Recon Premium | Ionix | Praetorian Chariot |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | jjroth | 14/10/2024 10:26 AM | jjroth | 14/10/2024 10:31 AM | Asset and Exposure Discovery | 1 | ||||||||||
| 2 | jjroth | 14/10/2024 10:24 AM | jjroth | 14/10/2024 03:13 PM | External and Internal Exposure Identification |
|||||||||||
| 3 | jjroth | 14/10/2024 03:12 PM | jjroth | 14/10/2024 03:12 PM | Identify external organizational exposures |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| 4 | jjroth | 14/10/2024 03:12 PM | jjroth | 14/10/2024 03:14 PM | Asset Discovery Methods |
|||||||||||
| 5 | jjroth | 14/10/2024 03:14 PM | jjroth | 14/10/2024 03:14 PM | Asset discovery |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| 6 | jjroth | 14/10/2024 03:14 PM | jjroth | 14/10/2024 03:14 PM | Passive Discovery |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| 7 | jjroth | 14/10/2024 03:14 PM | jjroth | 14/10/2024 03:14 PM | Active Discovery |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| 8 | jjroth | 14/10/2024 03:15 PM | jjroth | 14/10/2024 03:16 PM | IPv6 and Error Management |
|||||||||||
| 9 | Including IPv6 assets |
Yes | Yes | No | No | No | No | Yes | Yes | Yes | Yes | Yes | ||||
| 10 | Reduce False Positives |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 11 | jjroth | 14/10/2024 03:15 PM | jjroth | 14/10/2024 03:15 PM | Cloud and On-Premise Asset Discovery |
|||||||||||
| 12 | Discover unknown assets in cloud |
Yes | Yes | No | No | No | No | Yes | Yes | Yes | Yes | Yes | ||||
| 13 | Connection and Environment Mapping |
|||||||||||||||
| 14 | Fake Domains - Typosquating |
Yes | No | No | No | No | No | No | No | No | Yes | No | ||||
| 15 | jjroth | 14/10/2024 10:26 AM | jjroth | 14/10/2024 10:34 AM | Risk Assessment and Prioritization | 1 | ||||||||||
| 16 | Risk Evaluation and Scoring |
|||||||||||||||
| 17 | Predictive Risk Based |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 18 | AI Technology |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 19 | Risk-based Scoring |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 20 | Adversarial and Vulnerability Insights |
|||||||||||||||
| 21 | Adversarial insights |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 22 | Confirm CVEs exist |
Yes | Yes | Yes | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | ||||
| 23 | jjroth | 14/10/2024 10:26 AM | jjroth | 14/10/2024 10:35 AM | Security Testing and Continuous Monitoring | 1 | ||||||||||
| 24 | Multi-environment Monitoring |
|||||||||||||||
| 25 | Hybrid IT Environments |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 26 | Clouds |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 27 | Managed Platforms |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 28 | Third-party Services |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 29 | Extended Discovery |
|||||||||||||||
| 30 | Multi-layered engine |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 31 | Real-time visibility |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 32 | Noise Reduction |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 33 | Automated scans |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 34 | jjroth | 14/10/2024 10:27 AM | jjroth | 14/10/2024 10:35 AM | Consulting, Integration, and Cloud Services | 1 | ||||||||||
| 35 | Cloud Service Accessibility |
|||||||||||||||
| 36 | Convenient access |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 37 | Scalability without investments |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 38 | Swift flexibility |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 39 | jjroth | 14/10/2024 10:27 AM | jjroth | 14/10/2024 10:27 AM | Threat Management and Cyber Risk | 1 | ||||||||||
| 40 | Threat Detection and Management |
|||||||||||||||
| 41 | Zero-day visibility |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 42 | Risk Management Strategies |
|||||||||||||||
| 43 | M&A Risk Management |
Yes | Yes | No | Yes | Yes | Yes | No | No | Yes | Yes | Yes | ||||
| 44 | Due Diligence Risk Control |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 45 | Risk Exposure Analysis |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 46 | Cyber Risk Quantification and Management |
|||||||||||||||
| 47 | Risk Quantification |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 48 | Recursive assessment |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 49 | Deep evaluation |
Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 50 | jjroth | 14/10/2024 10:27 AM | jjroth | 14/10/2024 10:27 AM | Collaboration and Operational Optimization | 1 | ||||||||||
| 51 | Resource and Service Management |
|||||||||||||||
| 52 | Efficient resource allocation |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 53 | Comprehensive monitoring |
Yes | Yes | No | Yes | Yes | Yes | No | No | Yes | Yes | Yes | ||||
| 54 | Coverage: all vectors |
|||||||||||||||
| 55 | External |
Yes | Yes | No | No | Add-On | Add-On | Yes | Yes | Yes | Yes | Yes | ||||
| 56 | Cloud |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 57 | Web App |
Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 58 | Rogue IT |
Yes | Yes | No | No | No | No | Yes | Yes | Yes | Yes | Yes | ||||
| 59 | Supplier and vendor risk |
Yes | Yes | No | No | Add-On | Add-On | Yes | Yes | Yes | Yes | Yes | ||||
| 60 | jjroth | 14/10/2024 10:28 AM | jjroth | 14/10/2024 10:28 AM | Reporting, Support, and Community Engagement | 1 | ||||||||||
| 61 | Reporting and Insights |
|||||||||||||||
| 62 | Event Alerting |
Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 63 | Data export |
Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 64 | Scorecard summary reports |
Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes | ||||
| 65 | Historical trends and analysis reports |
Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 66 | Comparison and benchmarking reports |
Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 67 | Activity remediation log |
Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 68 | Enhanced Board Report |
Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes | ||||
| 69 | Report co-branding |
Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | No | No | ||||
| 70 | Support and Customer Success |
|||||||||||||||
| 71 | Help Center articles |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 72 | In-Platform Email Support |
Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes | ||||
| 73 | jjroth | 14/10/2024 10:28 AM | jjroth | 14/10/2024 10:28 AM | Risk and Security Assessments | 1 | ||||||||||
| 74 | Assessment and Scoring Systems |
|||||||||||||||
| 75 | A-F ratings |
Yes | No | Yes | Yes | Yes | Yes | No | No | No | No | No | ||||
| 76 | Issue Severity |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | ||||
| 77 | Ease of Use |
|||||||||||||||
| 78 | Red light, Green light Monitors |
Yes | No | No | No | No | No | No | No | No | No | No | ||||
| 79 | Overall Risk Score |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 80 | Industry Peer Comparison - 12 Month History |
Yes | Yes | Yes | Yes | Yes | Yes | No | No | No | No | No | ||||
| 81 | Detailed Data Breach Analytics |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | ||||
| 82 | jjroth | 14/10/2024 10:34 AM | jjroth | 14/10/2024 03:26 PM | Built-in Request Help Button |
Yes | No | No | No | No | No | No | No | No | No | No |
| Category | TARA CTA | Bitsight | Security Scorecard - Free | Security Scorecard - Business | Security Scorecard - Enterprise | Security Scorecard - Max | IBM - Security Randori Recon Essentials | IBM - Security Randori Recon Standard | IBM - Security Randori Recon Premium | Ionix | Praetorian Chariot |
Note: All information is based on publicly available information as of 6/2024. All copyrights are the property of their respective owners.