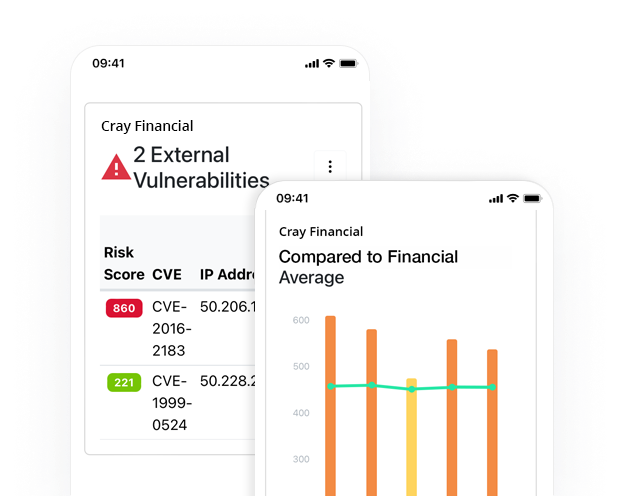
Establishing a process and dedicating resources (external or internal) for addressing TARA CTA findings is the first step toward fixing them. The key categories to focus on are Open Ports, Remote Desktop Services, and External Vulnerabilities as they represent the most risk exposure for organizations. Prioritizing vulnerabilities is simple since they are assigned a risk score. As a guideline any vulnerability with a score above 650 should be addressed as a top priority.